Migrate your tenant to Black Duck (with single sign-on)
If you use single sign-on to manage access to Polaris, you need to adjust your single sign-on settings in Polaris before you migrate to the Black Duck domain, and adjust single sign-on settings in your IDP after you migrate your tenant to the Black Duck domain.
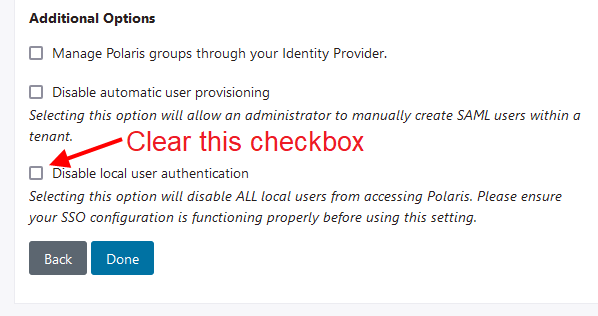
- Enabling local authentication for Organization Administrators.
- Running the migration.
- Downloading new SAML metadata from Polaris.
- Updating SSO settings in your IDP.
Each one of these steps is described in greater detail below.
Enable local authentication for Organization Administrators
Run the migration
Download new SAML metadata
- Go to .
- Select Download Metadata.
Update settings in your IDP
sso_saml_metadata.xml file, and use them to reconfigure single sign-on settings in your IDP. - The single sign-on URL for Polaris (found in the
Locationattribute ofmd:AssertionConsumerService). - The entity ID for Polaris (found in the
entityIDattribute ofmd:EntityDescriptor). - If you configured a single sign-out URL for Polaris, the single logout URL for Polaris (found in the
Locationattribute ofmd:SingleLogoutService).
Instructions for Azure (via Microsoft Entra ID) and Okta customers are included for reference:
Okta: update an app integration
Azure (via Microsoft Entra): update an enterprise application
Test your single sign-on settings
Troubleshooting
Can't sign into Polaris after running the migration
If you can't use your local credentials to sign into Polaris after you run the migration, you may be able to update SSO settings in your IDP manually. Completing this successfully will allow you to sign into Polaris using SSO.
The steps to complete this process vary from IDP to IDP, but you need to update 2-3 URLs in the SSO settings saved in your IDP:
- Service provider entity ID (for example, https://polaris.synopsys.com/auth/realms/docs)
- Single sign-on URL (for example, https://polaris.synopsys.com/auth/realms/docs/broker/sso/endpoint)
- (Optional) Single logout URL (for example, https://polaris.synopsys.com/auth/realms/docs/broker/sso/endpoint)
Replace "synopsys" with "blackduck" (for example, https://polaris.synopsys.com/auth/realms/docs > https://polaris.blackduck.com/auth/realms/docs) in these URLs and save your changes.
 | Dev Portal
| Dev Portal